If you are looking for a key fob system for your business, you have definitely seen decades of key upgrades, from alloys like brass, nickel, silver, and steel. And now you are ready to move to a verified, trackable access; A key fob.
A key fob access control system gives you control over who enters, when, and where. So you decide to grant access when a fob’s data is authenticated by a reader, which can be customized to restrict access to certain areas or grant temporary access.
Key fob systems offer benefits such as tracking entry logs and can be integrated with other security measures, such as CCTV, for enhanced security.
In this guide, we are also busting the biggest myths about key fob systems. From the belief that fobs can’t be hacked to the idea that cloud systems are less secure. You’ll see why modern encrypted fobs and remote video monitoring have changed the game entirely.
What is a key fob system?

A key fob is made of plastic with a small chip embedded. A keyless entry system allows you to open a door or enter a building without a physical key.
Each fob carries a unique digital credential linked to an employee profile in a secure cloud database. If that credential matches the stored permissions, the reader sends a signal to unlock the door.
Behind the scenes, the technology is powered by RFID (Radio Frequency Identification), NFC (Near Field Communication), or Bluetooth, enabling fast and contactless authentication. This not only accelerates entry during high-traffic hours but also strengthens security by eliminating the vulnerabilities of physical keys.
How does a key fob system work?
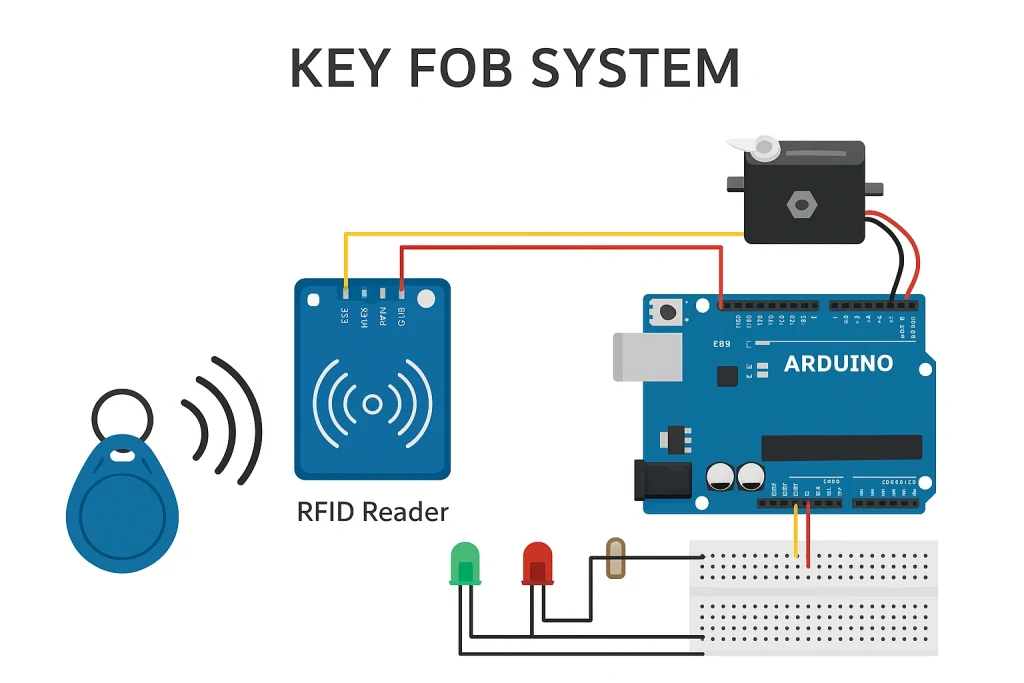
Credential assigning phase:
Each employee or authorized user receives a unique RFID, NFC, or Bluetooth key fob. These digital credentials are encrypted to prevent cloning and can be activated, updated, or revoked instantly through the admin dashboard.
Scan phase:
Key fobs contain a small chip that stores encrypted data. The system also includes a reader at each secured door that scans a key fob. The RFID reader detects a nearby key fob and reads its unique ID.
Authentication phase:
When a user presents their fob to the reader. The Arduino compares the scanned ID with a list of authorized IDs stored in the code. The system authenticates the fob’s identity and grants or denies access based on the configured permissions.
Decision phase:
- If the ID matches, the servo rotates to “unlock” the door, and the green LED turns on.
- If not, the red LED lights up, and the door remains “locked.”
Reset phase:
After a few seconds, the system resets, turning off the LED and returning the servo to the locked position.
What is a key fob security system for business?

A key fob security system for business is a modern, keyless entry solution that replaces mechanical locks.
A key fob access system is a fast and secure keyless solution for your gym, apartment complex, or office building.
You decide who is allowed to enter which area, building, or room of your premises. When an employee waves or taps their fob near an electronic reader, the system verifies their identity in milliseconds.
Why do you need to switch to key fob entry systems?
You want predictable and transparent costs:
The biggest headache in the Key fob entry system for buildings is rekeying locks and replacing lost keys. Also, when employees leave and do not hand back keys, it also creates a surveillance gap. With a key fob system, you can forecast your business’s total costs clearly: hardware, software, installation, and maintenance.
No need to worry about credential security:
Lost keys are easy to copy, but lost fobs are not. A secure key fob system for business uses encrypted RFID or NFC credentials that can’t be cloned.
Pair that with multi-factor authentication and compliance-ready data logs, and you’ve turned access control into a reliable defense layer.
You can’t afford downtime:
Power outages or internet drops shouldn’t lock your business out. A reliable key fob access control system includes PoE readers, battery backups, and offline modes that keep doors operational even when the network isn’t.
You want employees to actually use it:
The easier the system, the stronger your security. A user-friendly key fob system lets staff tap and go.
A professional key fob system installation for office environments can be done in a day or two, using wireless or PoE setups to minimize drilling and disruption.
You’re managing multiple sites:
Multi-location operations demand unified control. With a scalable access control system, you can manage credentials, track activity, and adjust permissions across all sites from a single dashboard.
It’s security without the complexity.
You need support that doesn’t stop after setup:
Security isn’t a one-time project, it’s an ongoing responsibility.
Choose vendors that offer continuous maintenance and support, remote monitoring, and guaranteed response times.
Consistent upkeep means fewer surprises and a system that performs flawlessly year-round.
You’re building a smarter security ecosystem:
When you adopt a key fob system, you are in fact upgrading to a smarter, data-driven approach.
By integrating access control with CCTV, AI analytics, and visitor management, you gain more than just entry logs. You also notice they’re gaining insight, efficiency, and peace of mind.
Are key fob access systems really reliable?
In April 2025, CBS News reported that tenants in an apartment complex were left locked out after their electronic fobs failed.
Around the same time, Drexel University’s Triangle covered mobile key failures in student housing, where connectivity glitches turned everyday access into daily frustration.
Older models can be cloned, shared, or simply fail when hardware glitches strike. A key fob system is only as reliable as its setup, maintenance, and oversight.
Newer systems now pair fobs with encrypted chips, mobile credentials, and cloud dashboards to close those security gaps.
Instead of relying on a single layer of security, businesses are combining multiple technologies. For example, an employee might tap a secure HID key fob, verify identity through a mobile app, and have their access automatically logged in a cloud dashboard.
Now what?
Many businesses upgrading their access control want reassurance that their existing systems can evolve without starting from scratch, and the good news is, they can.
Most modern key fob systems now integrate with cloud-based dashboards and software upgrades that add remote management, real-time alerts, and analytics to existing door hardware. If the power goes out, backup batteries and offline authentication keep doors functional so operations don’t stall.
How does remote video monitoring strengthen access control?

Remote Video Monitoring takes it to the next level. While key fob systems track who entered and when, video monitoring confirms who actually walked in.
If a cloned or stolen fob is used, live operators can verify the person on camera in real time and deny entry instantly.
That’s where remote video monitoring closes the loop. Smart cameras can instantly flag cloned fob attempts, detect tailgating incidents in real time, and even manually authorize entry when systems go offline.
AI security cameras at every entry point allow security teams to verify every access event in real time visually. Even if someone tries to use a cloned or borrowed fob, the monitoring team can spot the mismatch instantly and deny entry.
It also helps prevent tailgating when someone slips in right after an authorized person, by combining AI detection with live human oversight.
Beyond hacking or misuse, video monitoring also fills the gaps left by technical downtime or maintenance issues. When the key fob system goes offline, remote operators can still manage entry manually, keeping your business running smoothly.
And for growing businesses, the value goes beyond safety; it’s about accountability and insight. You see who’s coming in, when, and why, across every location, without needing to be there.
In short, pairing your key fob access control with remote video monitoring transforms it from a single layer of security into a complete, intelligent access ecosystem, one that’s harder to hack, easier to manage, and built to grow with your business.
Frequently asked questions for key fob system for businesses:
What is a FOB in access control?
A FOB in access control is a small, wireless device, usually a keychain tag or card, that uses RFID (Radio Frequency Identification) or NFC (Near Field Communication) technology to grant entry to secured areas.
Each fob carries a unique encrypted ID that a reader verifies before granting access.
For businesses, a key fob system replaces traditional locks with smart, trackable credentials, offering faster access, enhanced security, and real-time visibility into who enters your property.
How much does a key fob system cost for a business?
The cost of a key fob system for a business depends on several factors: hardware, software, the number of doors, and installation complexity.
- Small office. $1,500–$3,000 for 1–2 doors.
- Medium businesses. $3,000–$7,000 for multi-door setups.
- Extensive facilities. $10,000+ for cloud-managed or multi-site systems.
How does a key fob system work?
A key fob system for business uses RFID or NFC technology to identify and verify users.
When a fob is tapped near a reader, it transmits an encrypted signal to a control panel. The system checks the stored permissions and, if authorized, unlocks the door.
Modern systems also log each access event, creating a digital record that helps with audits, compliance, and security monitoring.
Are key fob entry systems secure from duplication or hacking?
Yes, modern key fob entry systems are secure when properly configured. Fobs using encrypted RFID chips or NFC smart credentials are highly resistant to cloning.
However, older 125 kHz fobs can be hacked or duplicated with inexpensive tools. To stay protected, choose encrypted credentials, enable multi-factor authentication, and update firmware regularly.
Can I integrate a key fob door entry system with my existing alarm or camera setup?
Absolutely. A key fob access control system can integrate with CCTV cameras, alarm systems, and visitor management software.
When integrated, every access event is paired with a matching video clip, giving you complete visibility and instant verification. Businesses often combine this setup with remote video monitoring for live oversight and real-time incident response.
What’s the difference between a keyless entry system and a key fob access system?
Both are keyless entry systems, but they differ in how users gain access:
- Keyless entry systems can include keypads, mobile apps, or biometric scanners.
- Key fob systems use small RFID or NFC devices that transmit encrypted data to unlock doors.
Conclusion:
Whether you’re securing an office, an apartment complex, or a retail space, a business key fob system offers the perfect balance of convenience and control.
When you integrate it with Remote Video Monitoring, key fob system becomes the first layer of security. The video analytics take it further by verifying identities, tracking activities in real time, and keeps your operations running smoothly, even when networks fail.
Contact us today for a free demo on how modern and AI oversight can help keep your business stays protected, connected, and future-ready.





