Access control failures do not usually start with a broken door or a hacked system. They start quietly, with lost cards, outdated access lists, and doors that trust the wrong people at the wrong time.
Most buildings still rely on access control systems designed for a different era. Servers sit in closets. Permissions are updated manually. Credentials are shared, forgotten, or never revoked. By the time a problem is noticed, access has already been misused.
Access Control as a Service changes that model.
It moves access out of the building and into a centralized, cloud-managed platform. Permissions update in real time. Credentials follow people, not hardware. Security teams regain visibility rather than react after the fact.
This guide explains what ACaaS is, why organizations are moving to it, and why traditional Keypad/PIN entry/access control is becoming a liability in modern environments.
What is access control as a service?
A cloud-based access control system means that onsite personnel manage door controllers, readers, locks, and other physical devices, while remote data centers host and process configuration, credential management, and logs.

On-site access hardware captures entry activity, while ACaaS cloud dashboards manage who can enter, when they can enter, and flag unusual behavior across all locations. So you can say you are renting access control as a service instead of building and managing it yourself.
System configuration of ACaaS:
ACaaS platforms use web or mobile-based dashboards to define policies for hardware such as swing doors and mantraps.
Next, they digitally map the physical hardware by assigning doors, readers, controllers, and sensors to virtual zones that represent real spaces such as entrances, offices, or secure areas.
Then, they define access policies and set schedules based on roles, for example, giving employees 24/7 access and limiting visitors to business hours.
After that, security rules are applied on top of those schedules. This can include controls like anti-passback to prevent credential sharing or duress codes for emergency situations.
Finally, the system syncs these policies in real time to the on-site devices, which immediately enforce the rules at the doors.
Each step builds on the last, turning physical hardware into a centrally managed, policy-driven access system.
Cloud credential management of ACaaS:
Administrators manage badges, mobile keys, PINs, and biometric identities through a centralized cloud portal.
HR or identity systems import user data in bulk and automatically assign roles and access permissions based on job function.
- Employee termination. When an employee is terminated or changes roles, the system revokes or updates their access within seconds, eliminating the need for manual follow-up.
- The system issues temporary credentials to vendors or contractors with predefined expiration times, ensuring access ends automatically when no longer needed.
Security teams apply additional security layers, such as multi-factor authentication, to high-risk doors and sensitive areas, strengthening protection where it matters most.
The result is a continuous, automated lifecycle for access credentials that reduces risk, improves efficiency, and enforces least privilege by default.
- Bulk import from HR systems auto-provisions roles (RBAC) for new hires, revoking on termination within seconds.
- Temporary vendor credentials expire automatically; multi-factor options layer on for high-security revolving doors.
Access control event logging:
Cloud-managed access control logs every access event 24/7, whether it’s a grant, denial, or forced door open. It automatically logs these events precisely, so you always have full information about user identities and timestamped supporting video snapshots.
- These centralized logs are fully searchable, making it easy to support compliance requirements such as PCI DSS audits.
- Retention policies define how long data is stored, such as ninety days, while secure exports preserve evidence for investigations without relying on local servers.
- The result is continuous visibility, audit readiness, and forensic capability without the burden of on-site infrastructure.
Why are businesses moving to ACaaS, and why does it matter?

Businesses are moving to ACaaS because they manage properties like platforms, not isolated sites.
Traditionally, access was about hardware on the doors. Panels in closets. A server in a back room. Software that only works from a specific computer inside the building.
The worst part was hard-wired control panels that connect every reader, lock, and exit device back to that server. Management happened locally. So if you had to add a credential, change a schedule, or run a report, someone would have to log in from a dedicated workstation inside the building.
Why ACaaS changes the equation?
Access Control as a Service shifts the center of gravity from the building to the organization.
Instead of a server in a closet, ACaaS software lives in the cloud. Thats cloud access control system where updates, backups, and security patches happen automatically. Management is remote by default. Adding a user or changing access does not require being on-site.
Hardware still exists at the door, but intelligence is centralized. Policies, schedules, and reporting are consistent across locations. A property manager can oversee one building or fifty from the same dashboard.
For condominiums and multifamily properties, this enables gradual unification. Mechanical keys can be reduced over time. Access becomes easier to revoke, audit, and transfer. Rekeying costs drop. Visibility improves.

For large commercial and multi-tenant buildings, ACaaS supports standardization. New tenants can be onboarded faster. Legacy systems can be phased out instead of frozen. Security becomes adaptable rather than static.
Most importantly, the model aligns with how businesses already consume technology. Software as a service is now the norm. Access control is simply catching up.
Why this shift matters:
Moving to ACaaS changes who controls access, how fast decisions are made, and how risk is managed. This shift reduces dependency on aging infrastructure, lowers friction across growing portfolios, and turns access control from a maintenance burden into a managed service.
Businesses are not leaving traditional access control because it failed. They are leaving because they outgrew it.
ACaaS matters because modern buildings are no longer isolated assets. They are part of connected, data-driven operations. Access control must evolve to match that reality.
Types of access control:
Based on authentication methods and deployment models for physical security, there are different types of access control.
Gate access control systems:
Gate access control systems are for pedestrian, vehicle, or hybrid traffic at main entrances, ranging from simple credentials to advanced barriers integrated with ACaaS platforms.
Authentication-based gate controls:
These verify users before activating gate operators:
Keypad/PIN entry:

Numeric codes on weatherproof panels; low-cost for residential condos but vulnerable to sharing.
RFID/proximity readers:

Long-range fobs or cards (up to 10ft) trigger swing/slide gates; standard for commercial lots.
Mobile credentials:

Smartphone NFC/Bluetooth apps open gates hands-free, managed via ACaaS dashboards.
Biometric scanners:

Facial or fingerprint units at pedestrian gates for high-security sites.
Vehicle access control:
Designed for cars/trucks at perimeter gates:
License Plate Recognition (LPR):
As a vehicle approaches the gate, cameras capture the license plate. The system reads the number and checks it against an approved list. If the vehicle is authorized, the gate opens automatically. If not, it stays closed. Every entry is recorded with time, plate number, and video for future review.
Tailgating detection AI for unauthorized vehicles:
Tailgating detection AI continuously monitors the entry lane with AI cameras. When one authorized vehicle enters and another slips in right behind it, the tailgating detection AI system detects the second vehicle. If the plate of that second vehicle is not approved, the system triggers an alert, and both the video feed and plate data are saved for investigation.
Integrated/enterprise systems:
Remote gate access control service offered by a top-notch remote video monitoring company is also a cloud-based ACaaS.
Access to the gate is managed by a live video monitoring company. It is a centralized management of LPR, intercoms, and barriers across sites.
They issue, distribute, and revoke mobile credentials or ID cards for drivers, syncing with LPR allowlists so that approved vehicles automatically open gates without user intervention.
Can ACaaS extend far beyond entry points?
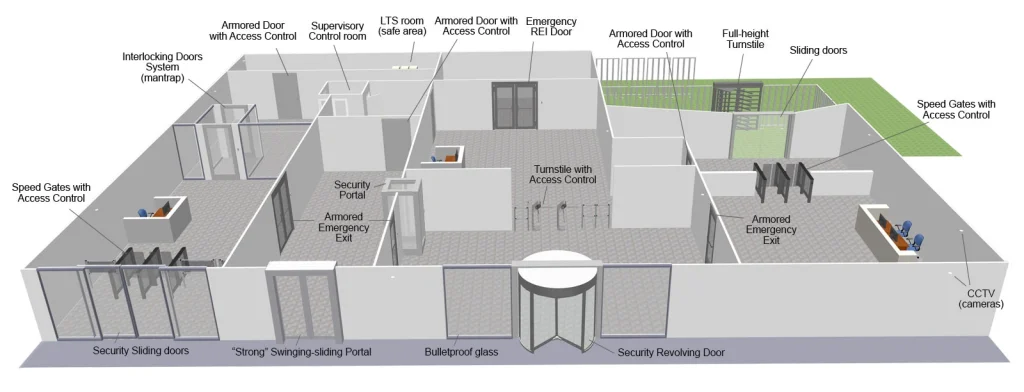
Yes, ACaaS extends far beyond entry points to secure internal areas, assets, and operations within facilities.
When people think about security, they usually focus on the main entrance.
But most security problems happen inside the building, not just at the front door.
Employees, contractors, residents, or visitors may be allowed into the building but should not be allowed everywhere.
This applies to offices, retail stores, warehouses, and condos.
Security must control where people can go, not just whether they can enter. Once inside, people can:
- Enter restricted offices or server rooms.
- Access cash handling or stock areas.
- Follow others into secure zones.
- Linger in places they should not be.
- Exit through the emergency doors improperly.
This is where internal doors, gates, and portals matter.
How each entrance can be secured with CCTV and video analytics?
ACaaS secures diverse physical access points like swing doors and turnstiles by integrating cloud-hosted management with on-site hardware such as readers, controllers, and locks.
Remote video monitoring centers link to these hardware devices. The advanced video analytics power the AI cameras.
A secured entry strategy ensures you are aware of every person who enters any door or gate. If that person isn’t authorized or authenticated, the security system handles it. Modern ACaaS integrates advanced video analytics to detect the following at various doors and entrances:
- They detect credential sharing when the same badge is used by different people.
- They flag forced entry when a door opens without a valid access event.
- They identify loitering and hesitation that often precede misuse or social engineering.
- They track route violations when someone enters an area they shouldn’t reach, even if the first door was authorized.
- They catch time based abuse, such as after hours access or repeated attempts that indicate probing.
- They monitor door misuse, like propped emergency exits or bypassed security portals.
Swing doors:
Standard hinged doors can be paired with badge readers or mobile credentials via ACaaS-compatible controllers. Cloud dashboards remotely assign time-based access (e.g., staff 9-5), log events, and trigger alarms on forced entry.
Turnstiles:
ACaaS supports waist-high turnstiles in lobbies and uses RFID for supervised flow, with ACaaS anti-passback rules locking out reuse. Full-height turnstiles at perimeters prevent over/under entry, managed centrally for compliance audits.
Revolving doors and mantraps:
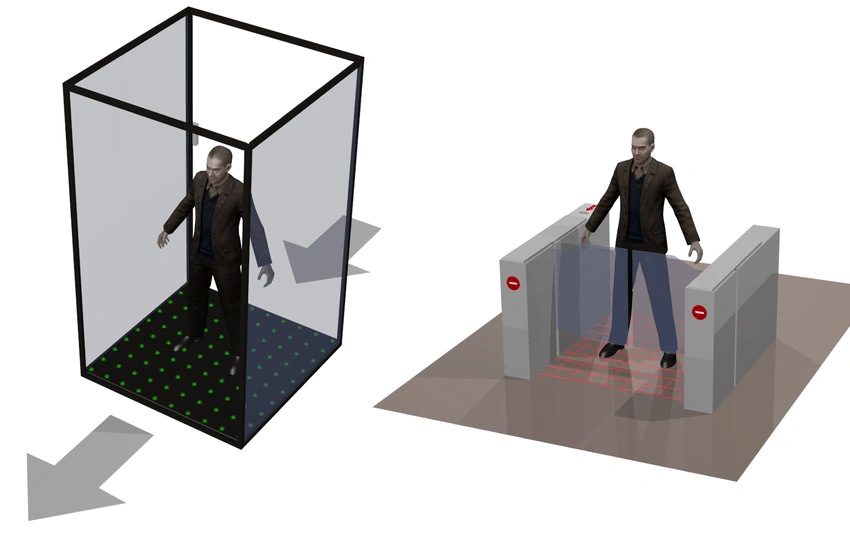
Revolving doors and interlocking mantraps enforce single occupancy by unlocking on credential scan. Second, secure the closing with integrated sensors and video verification.
Admins customize cloud rules for high-security zones and automatically lock on anomalies, such as detecting multiple bodies.
Employee, visitor, and perimeter points:
Admins assign RBAC (e.g., role-specific schedules) to employee doors, while they issue temporary QR codes to visitors via self-service portals.
Parking and gated perimeters:
For truck yards or retail backlots, LPR auto-opens for approved plates while alerting on unauthorized plates, reducing guard needs and providing entry/exit trails for logistics compliance.
What are the benefits of ACaaS?
Credential risk is reduced:
Mobile credentials, dynamic permissions, and instant revocation eliminate the impact of lost or stolen cards. Access follows the person, not the plastic, reducing tailgating and eliminating routine rekeying costs.
Access management stays accurate in real time:
Users are added, modified, or removed centrally and instantly. Role-based access ensures permissions always reflect current job status, not outdated spreadsheets or manual checklists.
Stronger defense against social engineering:
ACaaS supports multi factor authentication, mobile identity, and contextual rules that make shared credentials ineffective. Identity is verified continuously, not assumed.
Lower operational and maintenance overhead:
Cloud hosted software removes the need for on site servers, manual updates, and frequent service calls. Maintenance shifts from reactive hardware fixes to centralized system management.
Minimal downtime and faster recovery:
Cloud platforms update automatically and monitor system health continuously. Failures are detected early, and recovery does not depend on aging local infrastructure.
Built for scalability from the start:
Adding doors, buildings, or entire sites becomes a configuration task, not a construction project. Organizations can scale portfolios without redesigning their access architecture.
Smoother, faster user experience:
Mobile access, touchless entry, and smarter authentication reduce congestion at doors. Users no longer need to remember or replace physical cards.
Real-time visibility and alerting:
Every access event streams to centralized dashboards as it happens. Security teams can respond to anomalies immediately instead of discovering issues after the fact.
Designed for remote and hybrid operations:
Admins can securely manage access from anywhere. The system automatically issues and revokes temporary credentials for contractors, visitors, or hybrid staff.
Resilience during disruptions:
Cloud-managed systems are designed with redundancy and defined failover behavior. Access policies remain consistent and predictable during power or network interruptions.
The shift to ACaaS is not about adding features. It is about replacing a fragile, building-bound system with a resilient, identity-driven model that aligns with how modern organizations actually operate.
Frequently asked questions:
How does ACaaS handle offline door access and failover?
During outages, ACaaS controllers enforce the last-known access rules locally to maintain secure operation and sync events to the cloud once they restore connectivity.
How ACaaS reduces tailgating?
ACaaS integrates access events with video analytics to verify single-person entry, detect piggybacking in real time, and trigger immediate alerts or responses when misuse occurs.
Conclusion:
Access Control as a Service doesn’t add a new layer to old systems. It fundamentally shifts how businesses manage, verify, and enforce access.
By moving access control to the cloud, organizations gain real-time visibility, centralized control, and the ability to respond instantly to change. Credentials become dynamic. Policies stay accurate. Security teams stop reacting after the fact and start preventing misuse before it escalates.
Traditional access control was built for single buildings and static environments. ACaaS is designed for portfolios, mobility, and constant change.
Contact us today for a customized security solution for your business.





